Strategies for Securing Sensitive Information in Microsoft Teams
The role of Microsoft Teams has grown significantly over the past few years. Its seamless integration of chat, video conferencing, file sharing, and various productivity tools has become a popular platform for companies of all sizes. However, this increased usage also means a higher risk of exposing sensitive data. Confidential information such as financial records, client data, and intellectual property can flow through Teams, making it more vulnerable to breaches and misuse. To prevent such risks, companies need to adopt a proactive security approach. More is required to be aware of potential threats within Microsoft Teams. Companies must implement various security measures, from basic practices to advanced techniques, to ensure the data's confidentiality, integrity, and availability on the platform. By doing so, they can build a strong defense against cyberattacks and accidental data mishandling.
Foundational Best Practices
Advanced security techniques are crucial for keeping Microsoft Teams secure. However, it's equally essential to implement fundamental best practices to maintain a robust security strategy. The following practices form the foundation of a secure Microsoft Teams environment:
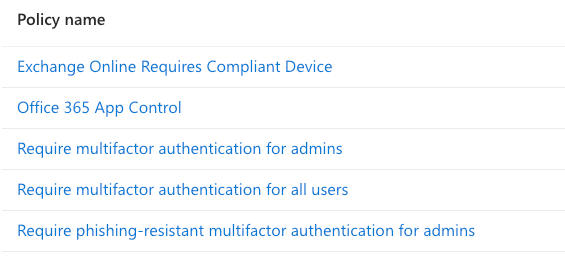
- Multi-factor authentication (MFA): To add a layer of security beyond simple passwords, MFA requires users to verify their identity using a code sent to their phone, an authenticator app, or a hardware token. It significantly reduces the risk of unauthorized access due to compromised passwords.
- Least privilege access: The principle of least privilege involves granting users only the minimum permissions they need to perform their job duties. This approach effectively limits the scope of potential damage if an account is compromised and helps to contain breaches.
- Strong password policies: Enforcing complex passwords (a mix of upper/lowercase letters, numbers, and symbols) and requiring regular password changes reduces the success of brute-force attacks. Use tools to block commonly used or easily guessed passwords to bolster security further.
- User awareness training: Your team is the first line of defense. Regular training on identifying phishing attempts, social engineering tactics, and other common threats is essential. Educate users about the importance of strong passwords, responsible data handling, and reporting suspicious activity.
Advanced Techniques for Data Protection
After implementing foundational best practices, it's essential to incorporate more advanced techniques in Microsoft Teams to protect sensitive information. Here are some of these techniques:
- Sensitivity labels: Sensitivity labels enable you to classify and safeguard your content within Teams. You can create labels such as "Confidential" or "For Internal Use Only" and set policies around them. These policies can enforce actions like encryption, watermarking, and access restrictions, ensuring your content is adequately protected based on its sensitivity.
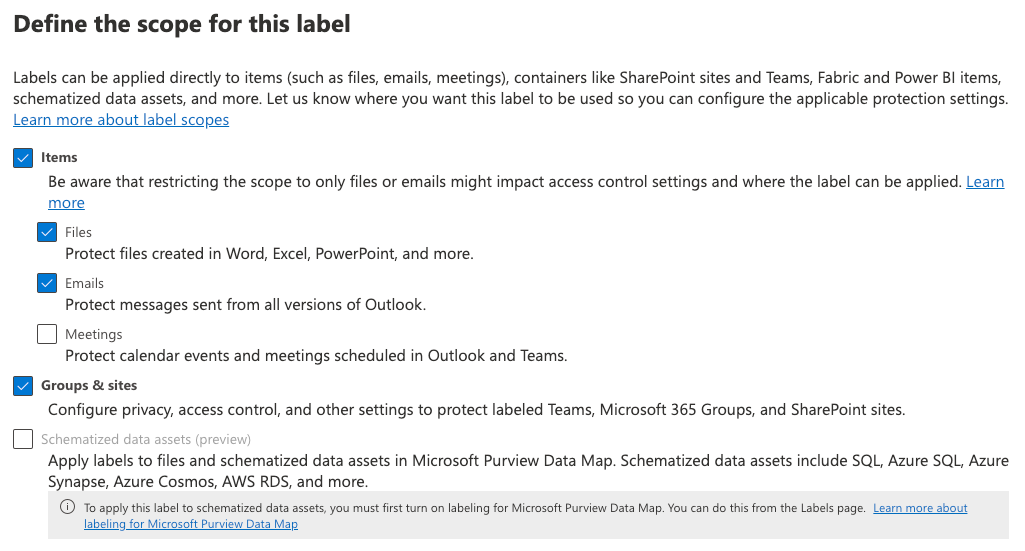
- Data loss prevention (DLP): DLP policies are proactive measures to prevent the accidental sharing or leakage of confidential information. For Teams, DLP policies can scan messages, files, and chats in real-time for sensitive data patterns such as credit card numbers, social security numbers, or other regulated information. They can automatically block the content, alert users, or notify admins if a violation is detected.
- Conditional access policies: Conditional access policies grant you granular control over who can access Teams and the conditions that permit access. These policies can consider user identity, device health, location, and risk level. For instance, you can restrict access to Teams from unmanaged devices or block logins from unusual locations.
- Information barriers: Information barriers benefit organizations with strict compliance requirements or a need to segregate communication between departments. They create virtual walls within Teams, preventing users in designated groups from communicating or sharing files. They can help enforce ethical walls and prevent insider threats.
Monitoring and Auditing
Vigilance is crucial to maintaining a strong security posture in Microsoft Teams. Regular monitoring and auditing activity logs help uncover potential threats and allow for swift responses.
It is crucial to enable auditing within the Microsoft Purview Compliance Portal to keep track of important events such as user activities, access attempts, file changes, administrative actions, and more. Regularly reviewing audit logs is essential to detect any suspicious activity. It is essential to pay attention to any red flags in the audit logs that could signal a breach or data misuse, such as unexpected logins from unfamiliar locations or devices, large file downloads or unusual data transfers, frequent failed login attempts, or changes to sensitive settings or permissions.
To streamline the process of aggregating and analyzing audit logs from Teams and other systems, use Security Information and Event Management (SIEM) solutions and other security analytics tools. These tools often utilize advanced capabilities such as machine learning to detect patterns that may indicate a security incident.
Additional Security Considerations
Beyond the core techniques already discussed, a comprehensive Teams security strategy should address additional considerations.
Using Teams, you can collaborate with people outside your organization through guest access. However, this also entails some risk. It is essential to evaluate carefully whether guest access is necessary and to limit their permissions to only what they need. Creating dedicated Teams with controlled permissions for interactions with external parties is advisable.
With the increasing use of mobile devices to access Teams, it is essential to implement an effective device management strategy. Microsoft recommends using Mobile Device Management (MDM) solutions. These solutions can help enforce security policies, manage app installations, and remotely remove data from a device in case it is lost or stolen.
Encryption is critical for protecting data in transit and at rest. Ensure proper configuration of Microsoft Teams' native encryption settings and consider additional encryption solutions for susceptible data.
Third-party apps can extend Teams' functionality, but they can also pose security threats. Establish a rigorous approval process, vet permissions, and monitor behavior.
Incident Response Planning
Data breaches and security incidents can happen despite the best preventive measures. Thus, having a predefined incident response plan is crucial to minimize damage and ensure quick recovery. A well-crafted response plan should outline the steps to take when a security incident occurs. It should include clear roles and responsibilities, communication protocols, and containment, investigation, and remediation procedures.
Effective communication during a security incident is critical, and a clear communication strategy is vital. The communication strategy should detail whom to notify, such as management, legal, and affected stakeholders, and how to disseminate information while minimizing confusion and panic.
Your incident response plan should include step-by-step instructions for investigating the breach, identifying its root cause, and containing the threat. It should also address remediation steps such as restoring backup data, resetting compromised accounts, and patching vulnerabilities.
To learn more about incident response, you can review the current Microsoft documentation:
- https://learn.microsoft.com/en-us/security/operations/incident-response-overview
- https://learn.microsoft.com/en-us/security/operations/incident-response-planning
Conclusion
Securing sensitive information within Microsoft Teams requires a comprehensive approach encompassing various best practices and advanced techniques. The foundational best practices include:
- Implementing multi-factor authentication.
- Using strong passwords, following the principle of least privilege.
- Providing user awareness training.
These practices lay the groundwork for a robust security strategy.
In addition to the foundational best practices, advanced techniques such as sensitivity labels, data loss prevention, conditional access, and information barriers provide additional layers of protection. Regular monitoring of audit logs and using security analytics tools help detect and mitigate potential threats.
It's crucial to remember that cybersecurity requires ongoing effort. Staying vigilant, adapting security practices as needed, and proactively adopting the measures discussed in this article can significantly improve your organization's security posture. It protects sensitive data housed within Microsoft Teams – a critical component for achieving success in the modern digital landscape.


